You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
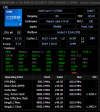
VMX enabled in bios, but showing "not supported" in HWINFO
- Thread starter didz
- Start date
Thank you Martin. Is this the same for SMX? And I notice TME is also shown to be supported and enabled... is this certain? Unfortunately there is no option for this in the bios...Yes, it's due to Hyper-V which intentionally masks presence of this feature.
Look in the screenshot, says HVCI disabled. I disabled secureboot. That shuts down HVCI. Its installed as an optional feature, but not active... windows system information and hwinfo both say disabled. I'll disable everything regardless when I have the time just to confirm what actually happens.Are you sure Hyper-V is completely disabled? Sometimes even after disabling HVCI, Hyper-V can remain active. The main window of HWiNFO should tell you whether Hyper-V is active.
Last edited:
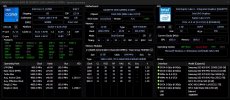
Appears that this turns out to not be true. Turns out Hyper-V was already disabled in optional features. So, I disabled "Windows Hypervisor Platform" instead, all device guard features via group policy, and secure boot, and the result is the same. Bcdedit hypervisorlaunchtype is also set to the default "auto". HWINFO is not listing VMX.Hyper-V can be active regardless of HVCI or Secure Boot state. Check the "Turn Windows features on or off".
Msinfo states,
security available: base virtualization support, secure boot, dma protection, secure memory overite, uefi code readonly, smm security mitigations 1.0, mode based execution control, apic virtualization
services running 'credential guard, hypervisor enforced code integrity, hardware-enforce stack protection (kernel-mode)
When I disable virtualization based security it shows none running.
What do you want me to look for in task manager?
security available: base virtualization support, secure boot, dma protection, secure memory overite, uefi code readonly, smm security mitigations 1.0, mode based execution control, apic virtualization
services running 'credential guard, hypervisor enforced code integrity, hardware-enforce stack protection (kernel-mode)
When I disable virtualization based security it shows none running.
What do you want me to look for in task manager?
No, because I reiterate, when I disable virtualization based security, (and secure boot) under "services running" it shows none running.This is quite odd as "Hypervisor Enforced Code Integrity" (HVCI) implies Virtualization is active.
Appears you are right, perhaps after enabling HVCI windows does a hellufa job to ensure it can't be bypassed. I ran hwinfo inside hirens boot cd, which is based on a windows 10 x64 pe environment, bypassing windows hvci, which allows to detect these hidden features. Does green signify they are enabled, or merely present?
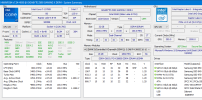

As noteted above, HWINFO (and coreinfo64) state SMX (aka TXT) is enabled, the latter at least says is 'capable'. However, windows event viewer states "Event 220, System Guard enabled but not supported. Reason: TXT is disabled by the BIOS in MSR_FEATURE_CONTROL."
How can it be disabled in the bios and still in the green? Partial but not full implementation? Improper detection? A software imposed limitation to promote VPRO?
How can it be disabled in the bios and still in the green? Partial but not full implementation? Improper detection? A software imposed limitation to promote VPRO?
Last edited:
Ok, but System Guard is not loading, which depends on TXT/SMX. Theoretically if the bit was disabled in the bios, windows should still load SMX? Are those features on top of SMX necessary for it to function properly? Can you name those features?Even Viewer probably means that SGX is disabled via MSR, not TXT. There are several features on top of SMX/TXT. MSR_FEATURE_CONTROL doesn't seem to be capable of disabling TXT.
Similar threads
- Replies
- 8
- Views
- 736
- Replies
- 2
- Views
- 376
- Replies
- 0
- Views
- 251